CISSP认证考试模拟试卷4
试卷名称:CISSP认证考试(通信安全与网络安全)模拟试卷1

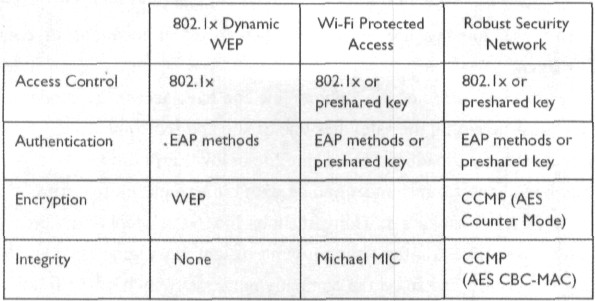
A.Service Set ID
B.Temporal Key Integrity Protocol
C.Ad hoc WLAN
D.Open system authentication
您可能感兴趣的题目
相关试卷
CISSP认证考试模拟试卷4
CISSP认证考试模拟试卷3
CISSP认证考试模拟试卷2
CISSP认证考试模拟试卷1
CISSP认证考试(软件开发安全)模拟试卷1
CISSP认证考试(访问控制)模拟试卷1
CISSP认证考试(信息安全治理与风险管理)模拟试卷1
CISSP认证考试(通信安全与网络安全)模拟试卷1
CISSP认证考试(安全体系结构和设计)模拟试卷1
CISSP认证考试(密码学)模拟试卷1
CISSP认证考试(物理安全与环境安全)模拟试卷1
CISSP认证考试(法律、法规、调查与合规)模拟试卷1
CISSP认证考试(业务连续性和灾难恢复)模拟试卷1
CISSP认证考试(安全运营)模拟试卷1